As one of today’s most popular social media platforms, YouTube is often in the crosshairs of cybercriminals who exploit it to peddle scams and distribute malware. The lures run the gamut, but often involve videos posing as tutorials about popular software or ads for crypto giveaways. In other scenarios, fraudsters embed links to malicious websites in video descriptions or comments, disguising them as genuine resources related to the video’s content.
Thefts of popular YouTube channels up the game further. By extending the reach of the fraudulent campaigns to untold numbers of regular YouTube users, they give the attackers the most bang for their buck. Cybercriminals have long been known to repurpose these channels to spread crypto and other scams and a variety of info-stealing malware, often through links to pirated and malware-laden software, movies and game cheats.
Meanwhile, YouTubers who have had their accounts stolen are in for a highly distressing experience, with the consequences ranging from loss of income to lasting reputational damage.
How can cybercriminals take over YouTube channels?
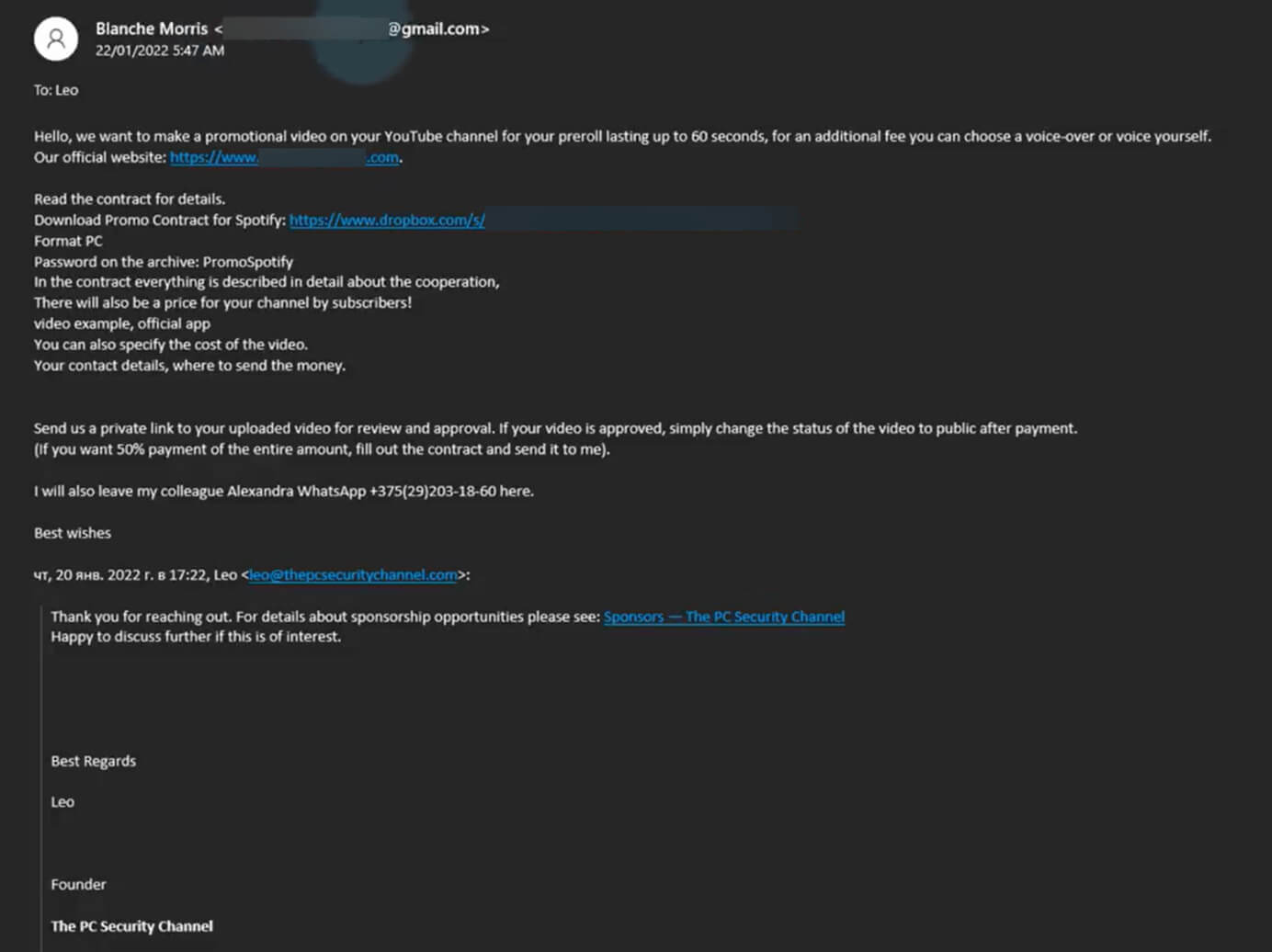
More often than not, it all starts with good ol’ phishing. Attackers create fake websites and send emails that look like they are from YouTube or Google and attempt to trick the targets into surrendering their “keys to the kingdom”. In many cases, they also tout sponsorship or collaboration deals as the lure – the message includes an attachment or a link to a file where the terms and conditions are said to be detailed.
Nothing could be further from the truth, however, with the threat becoming even more acute where the accounts were not protected by two-factor authentication (2FA) or where attackers circumvented this extra safeguard. (Since late 2021, content creators need to use 2FA on the Google account associated with their YouTube channel).
In some cases (cue the breach of Linus Tech Tips, a channel with 15 million subscribers at the time), attackers needed neither passwords nor 2FA codes to hijack the channels. Instead, they stole session cookies from the victims’ browsers that ultimately enabled them to bypass the additional security checks involved in the authentication process.
In another tried-and-tested technique, attackers leverage lists of usernames and passwords from past data breaches to break into existing accounts, relying on the fact that many people reuse passwords across different sites. In brute-force attempts, meanwhile, attackers use automated tools to try numerous password combinations until they find the correct one. This method yields fruits especially if people use weak or common passwords and skimp on 2FA.
Just weeks ago, the AhnLab Security Intelligence Center (ASEC) wrote about a growing number of cases where cybercriminals hijack popular YouTube channels, including one with 800,000 subscribers, and exploit them to distribute malware such as RedLine Stealer, Vidar and Lumma Stealer.
As described in the ESET Threat Report H2 2023, Lumma Stealer made a splash particularly in the second half of last year. This infostealer-for-hire is known for targeting crypto wallets, login credentials and 2FA browser extensions, as well as for exfiltrating information from compromised machines. As the ESET Threat Report H1 2024 shows, both tools remain a major menace and often pose as cheating software or video game cracks, including via YouTube.
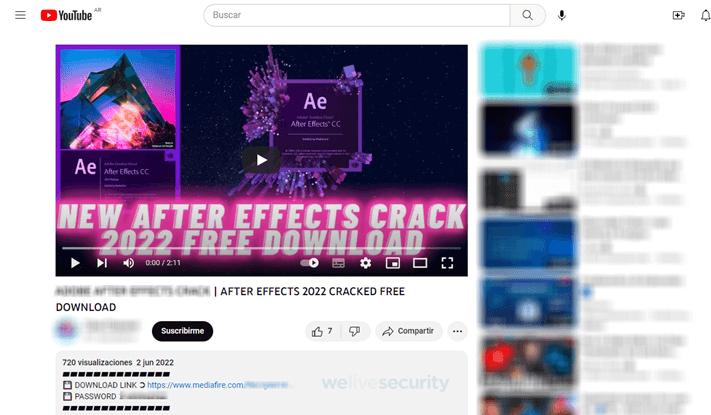
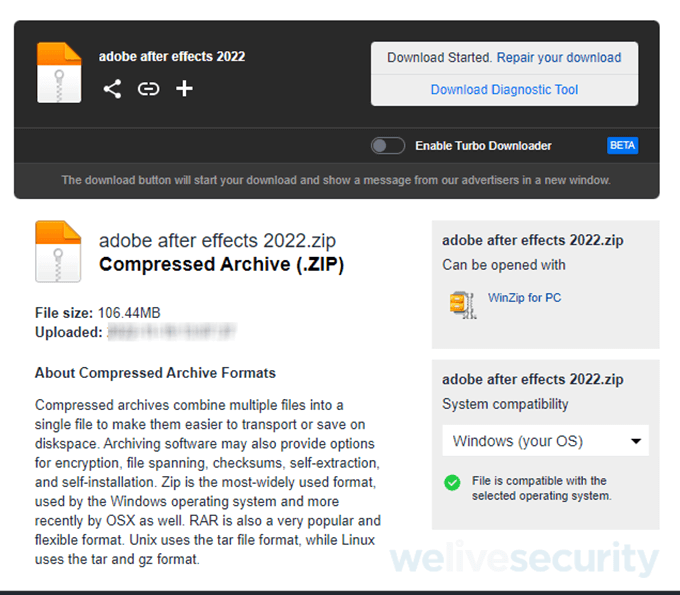
In some scenarios, criminals hijack existing Google accounts and in the span of minutes create and post thousands of videos that distribute info-stealing malware. People who fall victim to the attacks may end up having their devices compromised with malware that also steals their accounts on other major platforms such as Instagram, Facebook, X, Twitch and Steam.
Staying out of harm’s way on YouTube
These tips will go a long way towards keeping you safe on the platform, including if you’re a YouTuber yourself.
- Use strong and unique login credentials
Create strong passwords or passphrases and avoid reusing them across multiple sites. Explore passkeys as another form of authentication offered by Google.
- Use a strong form of 2FA
For an added layer of security, use 2FA not just on your Google account, but on all your other accounts. Wherever possible, choose 2FA involving authentication apps or hardware security keys instead of SMS-based methods.
- Be cautious with emails and links
Be skeptical of emails or messages claiming to be from YouTube or Google, doubly when they ask for your personal information or account credentials. Check the sender’s email address and look for signs of phishing. Just as importantly, avoid clicking on suspicious links or downloading attachments from unknown sources. The same goes for apps or other software that is promoted on YouTube unless they come from trusted and verified sources.
- Keep your operating system and other software updated
Ensure your operating system, browser, and other software are up to date to protect against known vulnerabilities.
- Keep tabs on your account activity
Regularly check your account activity for any suspicious actions or login attempts. If you suspect your channel has fallen prey to an attack, refer to this guidance from Google.
- Educate yourself
Stay informed about the latest cyberthreats and scams targeting you online, including on YouTube. Knowing what to look out for can help you avoid falling victim to these threats.
- Report and block suspicious content
Report any suspicious or harmful content, comments, links, or users to YouTube. Blocking such users can prevent them from contacting you further.
- Secure your devices
Use multi-layered security software across your devices to protect against a variety of threats.








